A new backdoor malware called BlackWater pretending to be COVID-19 information while abusing Cloudflare Workers as an interface to the malware’s command and control (C2) server.
Cloudflare Workers are JavaScript programs that run directly on Cloudflare’s edge so that they can interact with connections from remote web clients. These Workers can be used to modify the output of a web site behind Cloudflare, disable Cloudflare features, or even act as independent JavaScript programs running on the edge that displays output.
For example, a Cloudflare Worker can be created to search for text in a web server’s output and replace words in it or to simply output data back to a web client.
It is not known at this time how the file is being distributed, but it is most likely being done through phishing emails.
Inside this RAR file is a file called “Important – COVID-19.docx.exe” that uses a Word icon. Unfortunately, as Microsoft hides file extensions by default, many will simply see this file as a Word document rather than an executable and be more likely to open it.
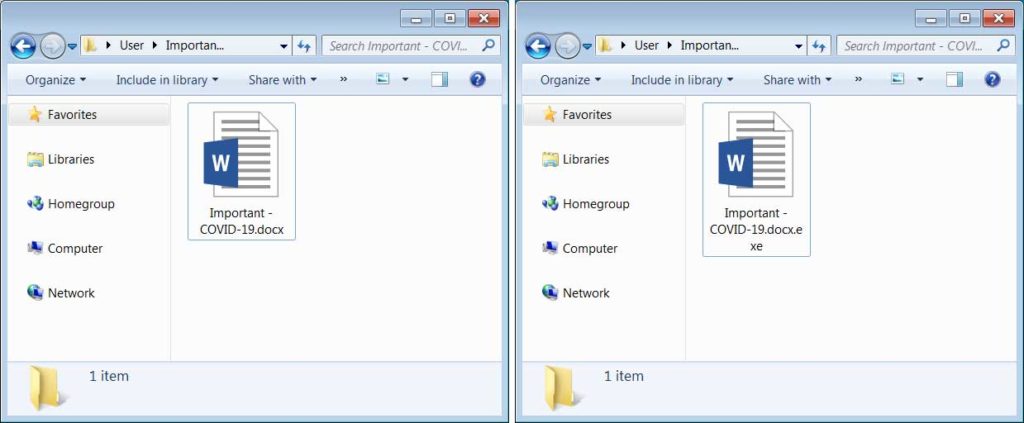
Extracted file with extensions off and on
When opened, the malware will extract a Word document to the %UserProfile%\downloads folder called “Important – COVID-19.docx.docx” and opens it in Word.
The opened document is a document containing information on the COVID-19 virus and is being used by the malware as a decoy as it installs the rest of the malware and executes it on the computer.
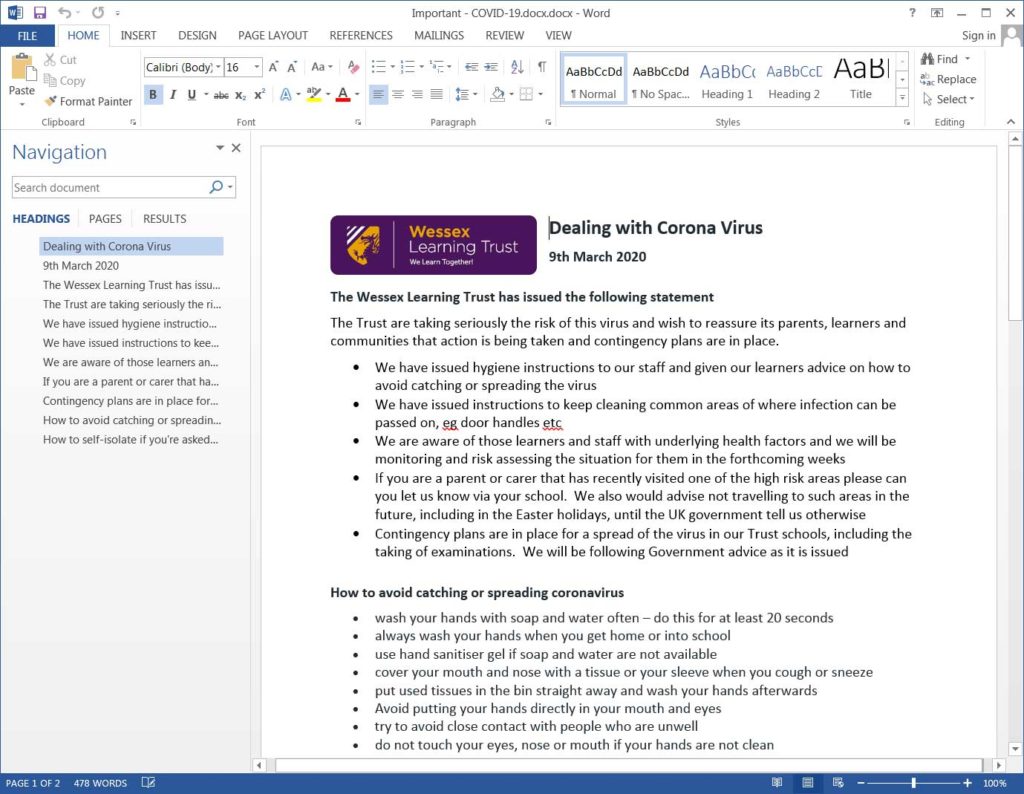
Decoy COVID-19 Information Document
While victims are reading the COVID-19 document, the malware is also extracting the %UserProfile%\AppData\Local\Library SQL\bin\version 5.0\sqltuner.exe file. This is where things get a bit interesting as the malware is then launched using a command line that causes the BlackWater malware to connect to a Cloudflare Worker that acts as a command and control server or at least a passthrough to one.
While there is still plenty to learn about this new malware and how it operates, it does provide an interesting glimpse of how malware developers are utilizing legitimate cloud infrastructure in novel ways.
Using Cloud Workers, traffic to malware command & control servers become harder to block and the malware operation can be easily scaled as needed.